<h1 class="entry-title">Category: Services</h1>
14
May

We develop and provide I.T. trainings that help us share our industry experience with fresh IT graduates and network administrators. This also helps participants understand real life problems and their remedies. Various free sessions and economical trainings are offered in the following areas: IT Career Path and Certifications Cabling for Corporate Network. Design of Corporate […]
14
May

A well designed and properly managed IT Infrastructure can easily fulfill the current needs, be flexible enough for expansion and be able to adapt to emerging technologies easily. Infrastructure implementation in most organizations is done as multiple small ad-hoc projects as the needs arise. Servers, workstations, and networking components are added without planning and considering […]
14
May

IT Infrastructure Audit and Assessment provides detailed and in-depth information to help the organization plan a strategy for smart IT investment. The weaknesses identified by the assessment can be helpful in developing a road-map for improvement in technology and processes. Our Baseline Assessment will be helpful in identifying and rectification of issue leading to improvement […]
14
May
Information Technology (IT) Infrastructure helps organizations in the delivery of IT services and information to the user’s desk at local and remote locations. Generally, the IT infrastructure refers to all the hardware and software that facilitate the delivery of IT services at the user’s desk for business operations. But it also includes many components that […]
14
May

Cybersecurity is a business issue and the top management is responsible for the development of the strategy for cybersecurity to meet the business objectives. Information Security (InfoSec) development and management are continuous processes of identifying, mitigating and preventing security issues. Security and vulnerability assessments are an integral part of developing a preventive mechanism to protect […]
14
May
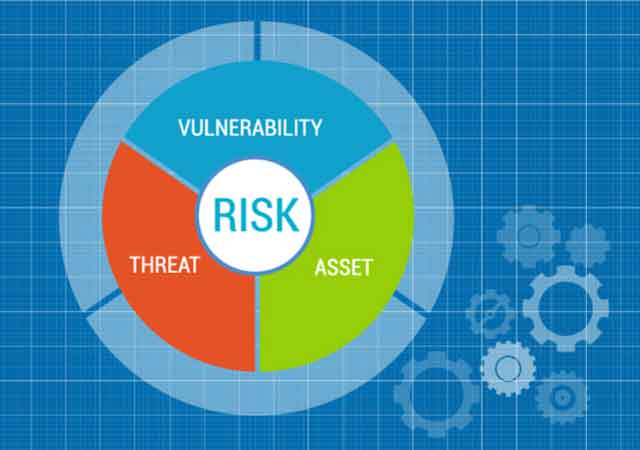
Information security assessment (also known as a security audit or security review) is a process of gap analysis between the level of security implemented and industry best practices. During the assessment, observation of vulnerability is made and presented to management with implication, risk level and recommended mitigation technique. After review of the report, management decides […]
14
May

Are you protected against Cyber Attacks? The need for protection of information and information processing system is growing with the growth of attacks by internal and external hackers. Cyber attacks are increasing in numbers and sophistication. Level of information security (InfoSec) must be evaluated regularly and updated to meet the new challenges and threats. Hackers […]
14
May

Managing IT system and services is a much more complex task than managing any other department. This is because it involves an understanding of the entire business operation and their needs, and converts them into technological requirements. Failure of IT services can cause failure of business operations in all other departments. IT systems and process […]








